
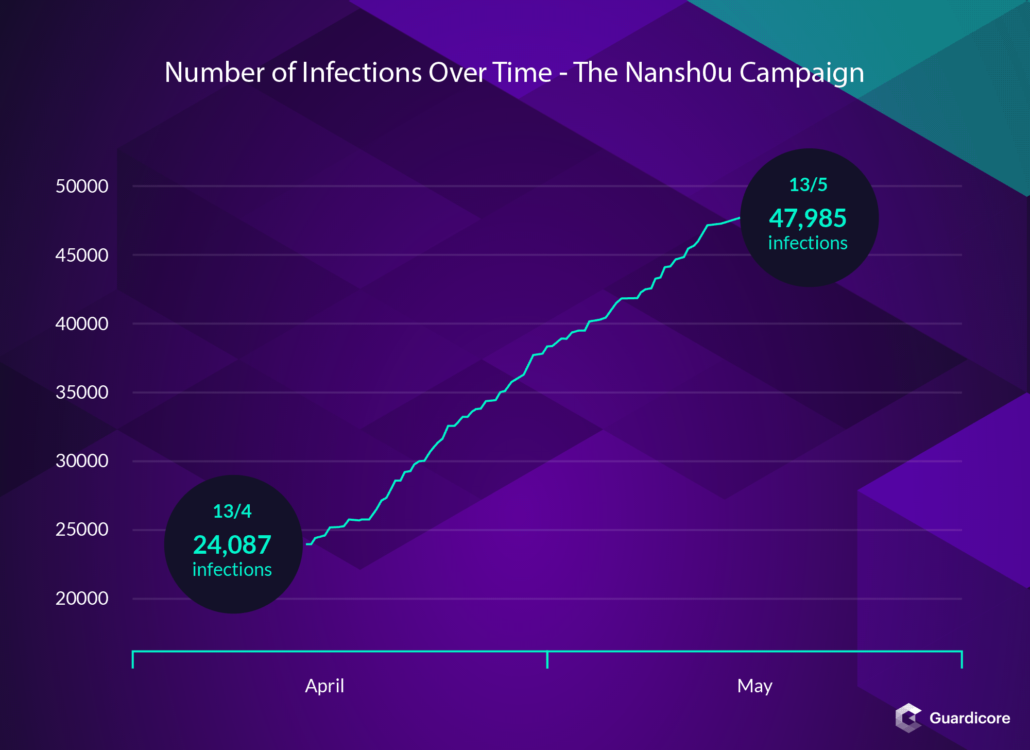
More than 50,000 MS-SQL and PHPMyAdmin were compromised by Chinese hackers and used to surreptitiously mine for TurtleCoin as part of a large-scale cryptojacking campaign dubbed Nansh0u.
The campaign was detected during early-April and it started as far back as back February 26, targeting servers located all over the world and belonging to companies from a wide range of industry sectors, "with over seven hundred new victims per day."
"During our investigation, we found 20 versions of malicious payloads, with new payloads created at least once a week and used immediately after their creation time," and the hackers used "five attack servers and six connect-back servers" according to the Guardicore Labs team which discovered the attacks.
The campaign is attributed by the Guardicore Labs team to Chinese operators based on multiple clues:
• The attacker chose to write their tools with EPL, a Chinese-based programming language.
• Some of the file servers deployed for this campaign are HFSs in Chinese.
• Many log files and binaries on the servers included Chinese strings, such as 结果-去重复 (“duplicates removed”) in logs containing breached machines, or 开始 (“start”) in the name of the script initiating port scans.
To compromise the Windows MS-SQL and PHPMyAdmin servers the hackers used a collection of tools comprised of a port scanner, an MS-SQL brute-forcing tool, and a remote execution module.
The port scanner allowed them to find MS-SQL servers by checking for default MS-SQL ports being open, servers which would automatically get fed into the brute-force tool which would attempt to break into the servers with the help of thousands of commonly-used credentials.
Once the servers were breached, the Nansh0u campaign operators would infect them with 20 different malicious payload versions using an MS-SQL script that would download and launch the payloads on the compromised machines.
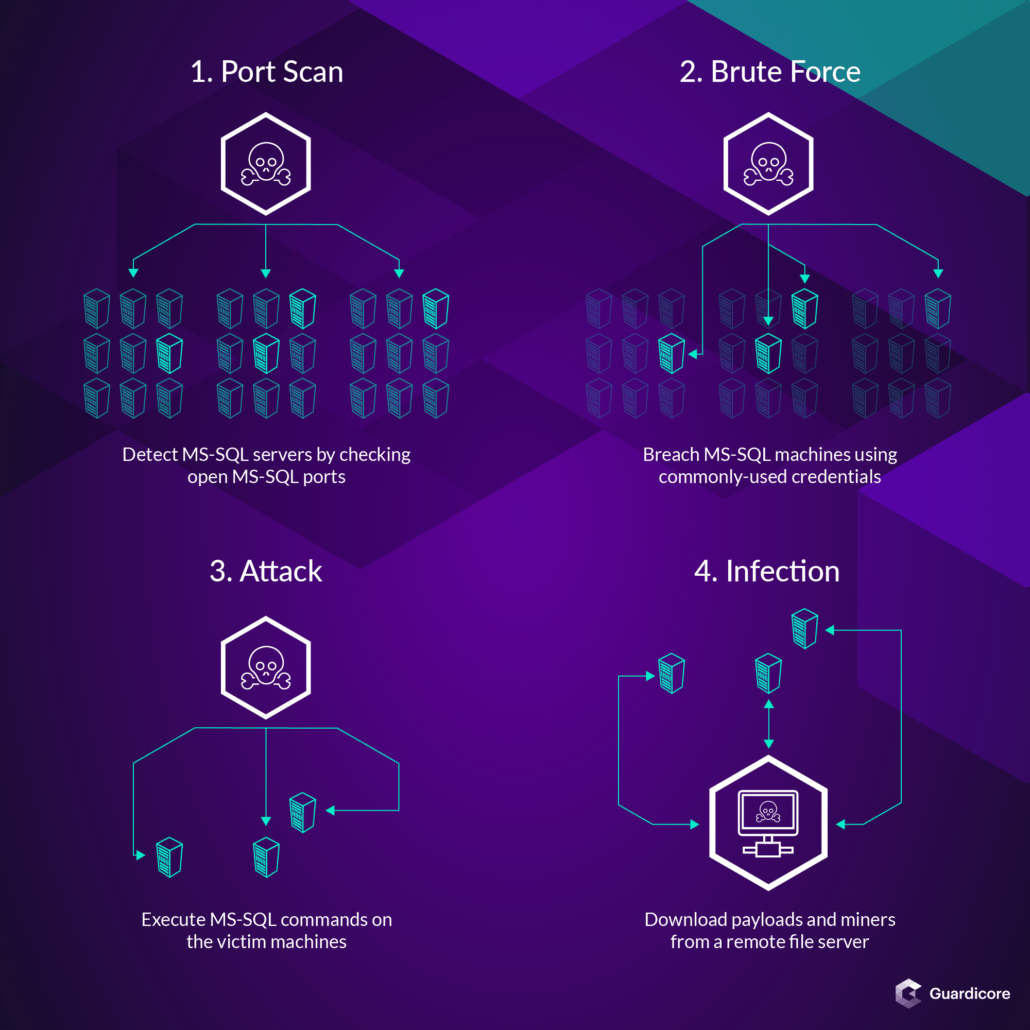
A privilege escalation vulnerability tracked as CVE-2014-4113 was exploited to run the payloads using SYSTEM privileges on the infected servers, with each of the dropped and executed payloads being designed as wrappers that would perform multiple actions.
As Guardicore's researchers discovered after analyzing the samples collected via the Guardicore Global Sensor Network (GGSN) and from the attack servers, the wrappers would:
• Execute the crypto-currency miner;
• Create persistency by writing registry run-keys;
• Protect the miner process from termination using a kernel-mode rootkit;
• Ensure the miner’s continuous execution using a watchdog mechanism.
The XMRig and JCE cryptocurrency miners use four mining pools to mine for TurtleCoin, a privacy-focused cryptocurrency with fast transactions and with every transaction being private unless made public.
A lot of the payloads dropped on the infected servers also dropped a randomly named and VMProtect-obfuscated kernel-mode driver which will evade detection by most AV engines.
The driver is also signed with a now-revoked certificate issued by Verisign to a Chinese company named Hangzhou Hootian Network Technology, and it is "designed to protect processes and prevent the user from terminating them."
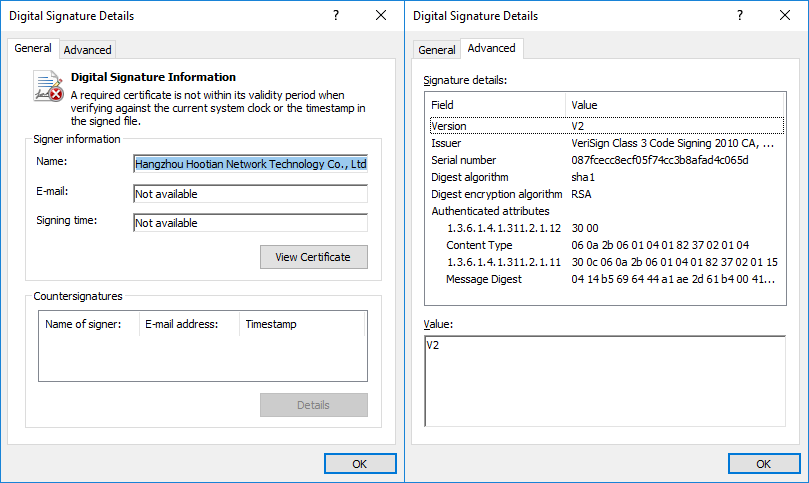
It also "contains additional rootkit functionality such as communicating with physical hardware devices and modifying internal Windows process objects that are unused by this particular malware."
In addition, the kernel-mode driver which made sure that the dropped malware will not be terminated, "supports practically every version of Windows from Windows 7 to Windows 10, including beta versions. This exhaustive coverage is not the work of a hacker writing a rootkit for fun."
The Guardicore Labs team provides a comprehensive IoC list for this cryptojacking campaign, including payload hashes, IP addresses used during the attacks, and mining pool domains.
A Powershell script designed to find residues left by the Nansh0u campaign on compromised machines is also provided to detect potentially infected servers.
"This campaign demonstrates once again that common passwords still comprise the weakest link in today’s attack flows. Seeing tens of thousands of servers compromised by a simple brute-force attack, we highly recommend that organizations protect their assets with strong credentials as well as network segmentation solutions," concludes the Guardicore Labs team.


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now