Having walked in the shoes of SOC analysts, I wanted to share some thoughts regarding the findings in our 2020 State of the SOC Report. The report covers several topics, including hiring and staffing, hard and soft skills, funding and budget, operational processes, and technologies.
Lack of leadership and communications may be contributing to staffing concerns
Our report indicated that 39% of respondents felt they were understaffed or severely understaffed. Of those who said they were understaffed, more than 30% said they were understaffed by 6-10 employees. Limited staff is a concern commonly expressed by SOC managers and frontline employees.
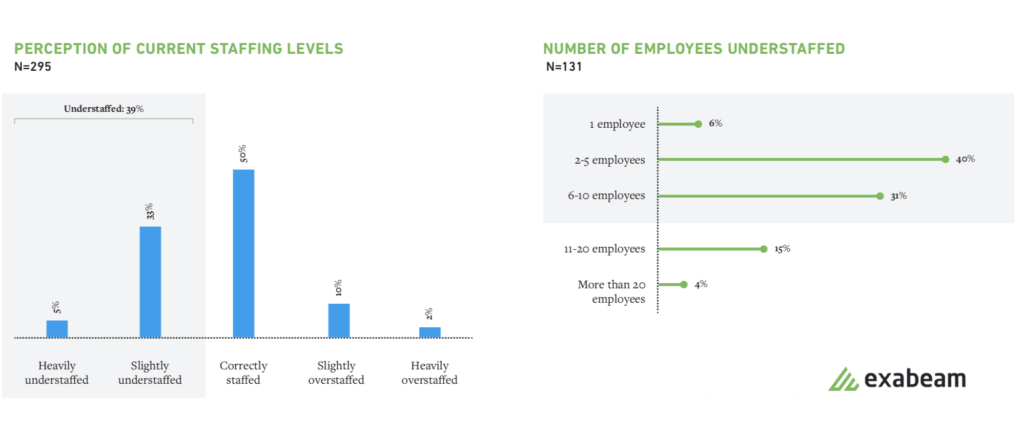
Figure 1: Thirty-nine percent of respondents feel they are understaffed; 30% of those said they were short by 6-10 employees.
In looking at related data, respondents noted an undefined career path and poor leadership were top reasons employees were difficult to retain.
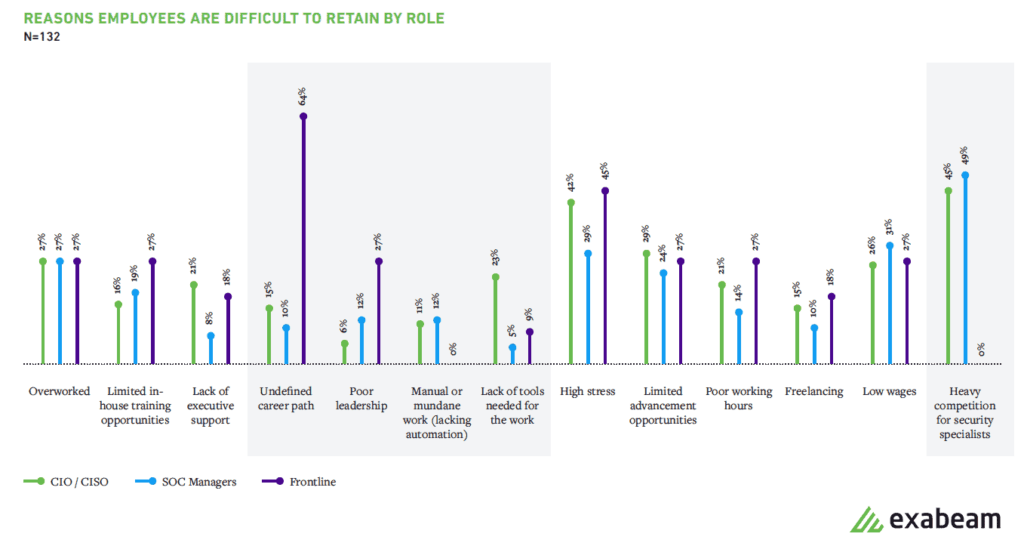
Figure 2: Employees say an undefined career path and poor leadership were top reasons for them to leave.
Leadership and communication issues may be contributing to staffing challenges. Some frontline workers (64%) believe their managers aren’t committed to helping them grow their careers. From the management perspective, 15% of C-level executives and 10% of SOC managers believed an undefined career path contributed to the difficulty in retaining their staff. Although cybersecurity positions have been around for quite some time, the industry itself is still rather immature and therefore leadership changes impact all employees beneath. Changes in the highest ranks (typical tenure for a CISO is 26 months) – lead to frustration among all staff reporting in that chain of command. Furthermore, uncertainty about changes in structure and roles leads to the notion of undefined career paths in an industry known for changing rapidly. This change makes cybersecurity both an exciting industry in which to work, but also a stressful and at times, tumultuous one.
Communication issues at any level in the chain of command can also cause a disconnect between the message analysts are trying to convey versus what a leader ultimately receives. This can make the job for leaders who already face many difficult decisions a whole lot more difficult to get it right. This rift sometimes causes downstream employees to feel that they are being ignored or undervalued in their contributions. As a result, analysts may feel their managers aren’t confident in their abilities to prioritize and respond to security incidents.
Increasing threat modeling effectiveness
The 2020 Report reveals a significant decline in SOC’s threat modeling effectiveness compared to 2018 and 2019. The drop may be a result of the lack of standardization. There are at least ten different types of threat models. At Exabeam, we’re doing a couple of things that will help our clients improve the effectiveness of threat modeling. First, we offer workshops led by solutions engineers who drill down into how to conduct threat hunting investigations that are standardized and repeatable. Second, we use MITRE ATT&CK as a framework to compare threat actor activity and develop defensive postures utilizing the intersection of both to define priorities for SOC initiatives.
Further, larger organizations often have a red-team or even a purple team that leverages threat modeling to determine how well their organizations can detect and respond to attacks. However, the data from these teams may only be visible to select analysts, an individual SOC manager, or to a lesser extent, to CIOs and CISOs. These insights need to be visible to the entire SOC team to reduce the likelihood and minimize the impact of cyberattacks.
Another interesting data point from the report is the disparity between management and frontline staffers’ view regarding their SOC’s “ability to detect threats.” Frontline staffers rated their ability to detect threats much lower than their bosses. Frontline employees could be unsure about how to investigate. Or perhaps, they’re disillusioned as many findings from their investigations result in dead-ends or get dismissed quickly by the next level analyst or manager.
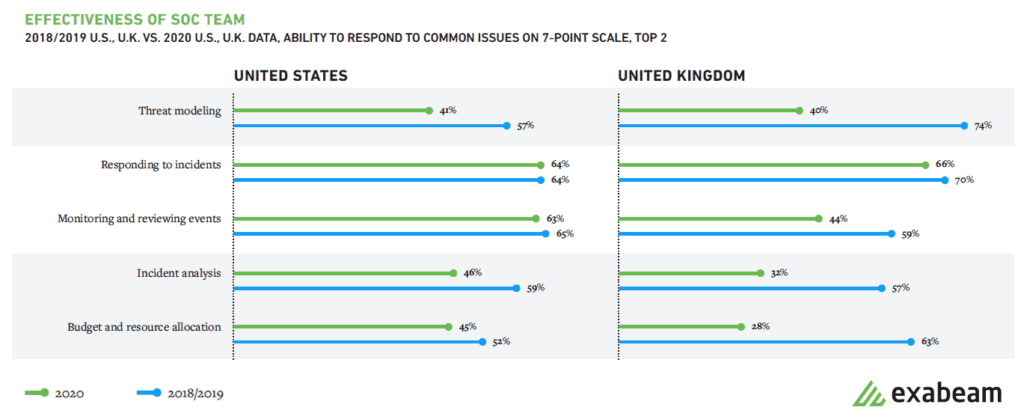
Figure 3: The perception of the team’s effectiveness to conduct threat modeling, incident analysis and budget and resource allocation dropped in the U.S. and the U.K. compared to 2019.
SOC pain points highlight inefficiencies
Higher rated pain points noted in the report, including “inexperienced staff”, “out-of-date systems/apps” and “time spent on reporting/documentation” are not surprising as these are common problems in any environment and need to be managed according to defined risk tolerances. On the other hand, pain points such as lacking asset lists, finding system owners, and manual attack timeline creation highlight inefficiencies that most SOCs experience; but also have direct control or influence to improve. While these sound straightforward, they have a meaningful impact on a SOC’s capability for TTA (time to answer) since it may only take a few minutes to look up an owner of a system, but in aggregate, these manual activities cause material lag during an investigation.
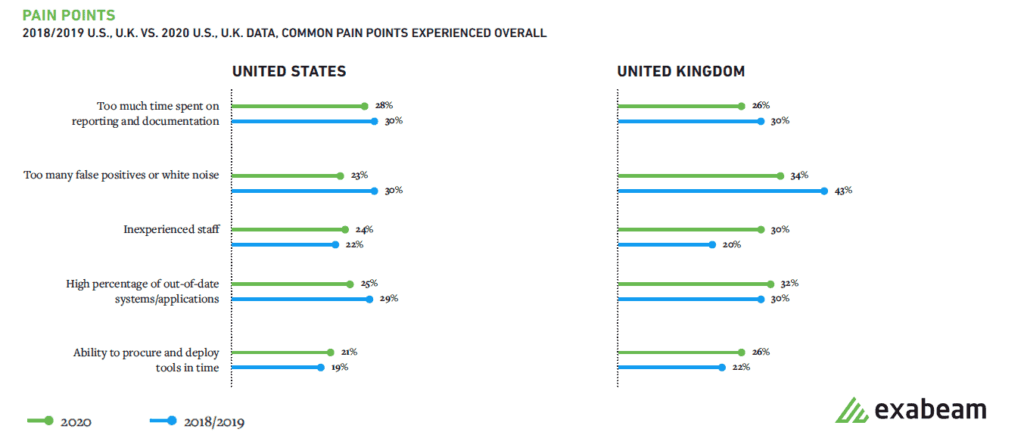
Figure 4: Inexperienced staff, out-of-date apps and time spent on reporting and documentation are top pain points for SOC teams.
The changing threat landscape and security technologies will always present challenges for SOCs. As a result, findings from peer surveys such as Exabeam’s report are valuable tools to help SOCs recognize these issues and make adjustments to address these multi-dimensional problems. I encourage you to read the “State of the SOC report.”
Similar Posts
Recent Posts
Stay Informed
Subscribe today and we'll send our latest blog posts right to your inbox, so you can stay ahead of the cybercriminals and defend your organization.
See a world-class SIEM solution in action
Most reported breaches involved lost or stolen credentials. How can you keep pace?
Exabeam delivers SOC teams industry-leading analytics, patented anomaly detection, and Smart Timelines to help teams pinpoint the actions that lead to exploits.
Whether you need a SIEM replacement, a legacy SIEM modernization with XDR, Exabeam offers advanced, modular, and cloud-delivered TDIR.
Get a demo today!











